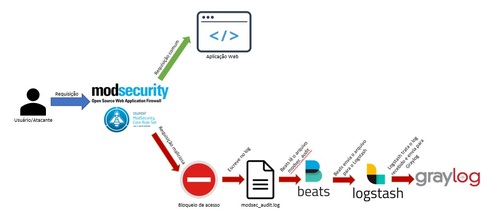
Implementação de WAF mod_security e integração com Graylog utilizando Filebeat e Logstash
Instalar e configurar um WAF utilizando mod_security em um servidor de proxy reverso para bloquear acessos maliciosos. Também é mostrado como integrar os logs gerados com o Graylog, a fim de obter uma melhor visibilidade dos ataques. Essa integração é feita com FileBeat e Logstash e o tratamento dos dados com o projeto logstash-modsecurity.
[ Hits: 10.327 ]
Por: NerdBarbado em 30/07/2020
Testando integração do modsecurity, filebeat e logstash
O mod_security verifica uma requisição maliciosa para os sistemas que estão "atrás" dele e gera uma entrada no arquivo de log /var/log/httpd/modsec_audit.log. O Filebeat tem configurado o arquivo de log do mod_security como input e como output o Logstash. O Logstash por sua vez tem um input configurado para receber dados do Filebeat, utilizar os filtros do projeto bitsofinfo /logstash-modsecurity para agrupar o log e organizá-lo em chaves-valores, enviando-os para seus outputs, um arquivo de log e o Graylog com o padrão GELF. Sendo assim, deixe aberto o arquivo de log do mod_security:
sudo tail -f /var/log/httpd/modsec_audit.log
Abra uma nova conexão com esse servidor e deixe o arquivo de log do Logstash aberto também, para verificar como será a output depois de todo o tratamento do log do mod_security.
sudo tail -f /var/log/logstash/logstash-output.log
Então, crie uma terceira conexão com o servidor e execute a linha abaixo, substituindo pelo endereço do seu sistema web protegido pelo mod_security. Isso irá criar uma requisição que parece maliciosa, disparando o mod_security:
sudo curl -s -o /dev/null -w '%{http_code}' " teste.com.br?username=1'%20or%20'1'%20=%20'"
Com isso, verifique a janela em que deixou o log do mod_security aberto. Devem ter sido geradas algumas entradas parecidas com as do exemplo abaixo:
--747c4d79-A--
[20/May/2020:15:40:42 --0300] XswRKrhtnI6jCBWSyb0URAAAAAE 192.168.0.3 59266 192.168.0.1 80
--747c4d79-B--
GET /?username=1'%20or%20'1'%20=%20' HTTP/1.1
User-Agent: curl/7.29.0
Host: teste.com.br
Accept: */*
--747c4d79-F--
HTTP/1.1 403 Forbidden
Content-Length: 202
Content-Type: text/html; charset=iso-8859-1
--747c4d79-E--
--747c4d79-H--
Message: Warning. detected SQLi using libinjection with fingerprint 's&sos' [file "/etc/httpd/modsecurity.d/owasp-modsecurity-crs/rules/REQUEST-942-APPLICATION-ATTACK-SQLI.conf"] [line "68"] [id "942100"] [msg "SQL Injection Attack Detected via libinjection"] [data "Matched Data: s&sos found within ARGS:username: 1' or '1' = '"] [severity "CRITICAL"] [ver "OWASP_CRS/3.2.0"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-sqli"] [tag "paranoia-level/1"] [tag "OWASP_CRS"] [tag "OWASP_CRS/WEB_ATTACK/SQL_INJECTION"] [tag "WASCTC/WASC-19"] [tag "OWASP_TOP_10/A1"] [tag "OWASP_AppSensor/CIE1"] [tag "PCI/6.5.2"]
Message: Access denied with code 403 (phase 2). Operator GE matched 5 at TX:anomaly_score. [file "/etc/httpd/modsecurity.d/owasp-modsecurity-crs/rules/REQUEST-949-BLOCKING-EVALUATION.conf"] [line "91"] [id "949110"] [msg "Inbound Anomaly Score Exceeded (Total Score: 5)"] [severity "CRITICAL"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-generic"]
Message: Warning. Operator GE matched 5 at TX:inbound_anomaly_score. [file "/etc/httpd/modsecurity.d/owasp-modsecurity-crs/rules/RESPONSE-980-CORRELATION.conf"] [line "86"] [id "980130"] [msg "Inbound Anomaly Score Exceeded (Total Inbound Score: 5 - SQLI=5,XSS=0,RFI=0,LFI=0,RCE=0,PHPI=0,HTTP=0,SESS=0): individual paranoia level scores: 5, 0, 0, 0"] [tag "event-correlation"]
Apache-Error: [file "apache2_util.c"] [line 271] [level 3] [client 192.168.0.3] ModSecurity: Warning. detected SQLi using libinjection with fingerprint 's&sos' [file "/etc/httpd/modsecurity.d/owasp-modsecurity-crs/rules/REQUEST-942-APPLICATION-ATTACK-SQLI.conf"] [line "68"] [id "942100"] [msg "SQL Injection Attack Detected via libinjection"] [data "Matched Data: s&sos found within ARGS:username: 1' or '1' = '"] [severity "CRITICAL"] [ver "OWASP_CRS/3.2.0"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-sqli"] [tag "paranoia-level/1"] [tag "OWASP_CRS"] [tag "OWASP_CRS/WEB_ATTACK/SQL_INJECTION"] [tag "WASCTC/WASC-19"] [tag "OWASP_TOP_10/A1"] [tag "OWASP_AppSensor/CIE1"] [tag "PCI/6.5.2"] [hostname "teste.com.br"] [uri "/"] [unique_id "XswRKrhtnI6jCBWSyb0URAAAAAE"]
Apache-Error: [file "apache2_util.c"] [line 271] [level 3] [client 192.168.0.1] ModSecurity: Access denied with code 403 (phase 2). Operator GE matched 5 at TX:anomaly_score. [file "/etc/httpd/modsecurity.d/owasp-modsecurity-crs/rules/REQUEST-949-BLOCKING-EVALUATION.conf"] [line "91"] [id "949110"] [msg "Inbound Anomaly Score Exceeded (Total Score: 5)"] [severity "CRITICAL"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-generic"] [hostname "teste.com.br"] [uri "/"] [unique_id "XswRKrhtnI6jCBWSyb0URAAAAAE"]
Apache-Error: [file "apache2_util.c"] [line 271] [level 3] [client 192.168.0.1] ModSecurity: Warning. Operator GE matched 5 at TX:inbound_anomaly_score. [file "/etc/httpd/modsecurity.d/owasp-modsecurity-crs/rules/RESPONSE-980-CORRELATION.conf"] [line "86"] [id "980130"] [msg "Inbound Anomaly Score Exceeded (Total Inbound Score: 5 - SQLI=5,XSS=0,RFI=0,LFI=0,RCE=0,PHPI=0,HTTP=0,SESS=0): individual paranoia level scores: 5, 0, 0, 0"] [tag "event-correlation"] [hostname "teste.com.br"] [uri "/"] [unique_id "XswRKrhtnI6jCBWSyb0URAAAAAE"]
Action: Intercepted (phase 2)
Apache-Handler: proxy-server
Stopwatch: 1590432042490279 2272 (- - -)
Stopwatch2: 1590432042490279 2272; combined=1550, p1=502, p2=867, p3=0, p4=0, p5=180, sr=103, sw=1, l=0, gc=0
Response-Body-Transformed: Dechunked
Producer: ModSecurity for Apache(http://www.modsecurity.org/); OWASP_CRS.
Server: Apache/(CentOS) OpenSSL/1.0.2k-fips
Engine-Mode: "ENABLED"
--747c4d79-Z--
Agora abra o arquivo de log dos outputs do Logstash, devem ter sido acrescentadas linhas parecidas com abaixo:
{"event_date_seconds":1.590432042490279E9,"responseStatus":"403 Forbidden","ecs":{"version":"1.5.0"},"rawSectionE":"","rawSectionH":"Message: Warning. detected SQLi using libinjection with fingerprint 's&sos' [file \"/etc/httpd/modsecurity.d/owasp-modsecurity-crs/rules/REQUEST-942-APPLICATION-ATTACK-SQLI.conf\"] [line \"68\"] [id \"942100\"] [msg \"SQL Injection Attack Detected via libinjection\"] [data \"Matched Data: s&sos found within ARGS:username: 1' or '1' = '\"] [severity \"CRITICAL\"] [ver \"OWASP_CRS/3.2.0\"] [tag \"application-multi\"]
Caso consiga verificar que os logs foram gerados corretamente, como nos exemplos acima, passe para a próxima etapa. Caso não, procure por erros nos seguintes:
- mod_security: /var/log/httpd/modsec_audit.log e /var/log/httpd/modsec_debug.log
- Logstash: /var/log/logstash/logstash-plain.log
2. Instalação e configuração do mod_security e mod_evasive
3. Instalação e configuração do FileBeat e Logstash
4. Testando integração do modsecurity, filebeat e logstash
5. Integração com o Graylog
Teste de Intrusão com Metasploit
Inprotect + Nessus: Scanner de vulnerabilidades
YASG (Yet Another Security Guide)
Entrevista com um hacker, via Internet
Fala amigo,
Primeiramente obrigado pelo artigo.
Uma observação:
Na parte "IncludeOptional modsecurity.d/rules/*.conf" seria "IncludeOptional modsecurity.d/owasp-modsecurity-crs/rules/*.conf"
Na parte "Ainda no arquivo /etc/httpd/modsecurity.d/mod_security.conf verifique..." o caminho do arquivo está errado. Seria o caminho /etc/httpd/conf.d/mod_security.conf
Atenciosamente,
x.x
run rabbit run
Patrocínio
Destaques
Artigos
Papagaiando o XFCE com temas e recursos
WhatsApp com Chamadas no Linux via Waydroid
XFCE - quase um Gnome ou Plasma mas muito mais leve
LXQT - funcional para máquinas pererecas e usuários menos exigentes
Dicas
Gentoo: Sincronização com Git e Automação via Systemd
Instalação do tema Fluent GTK no Zorin OS
PKI na Prática: Criando CA e Certificado Wildcard (Automatizado)
Tópicos
Midia de instalação LM-21.3 não inicializa (13)
eu queria saber no lenovo slim, se tem como ver os mhz de memoria e tu... (3)
Top 10 do mês
-

Xerxes
1° lugar - 118.443 pts -

Fábio Berbert de Paula
2° lugar - 55.529 pts -

Buckminster
3° lugar - 25.712 pts -

Mauricio Ferrari (LinuxProativo)
4° lugar - 18.256 pts -

Sidnei Serra
5° lugar - 17.715 pts -

Alberto Federman Neto.
6° lugar - 17.683 pts -

Alessandro de Oliveira Faria (A.K.A. CABELO)
7° lugar - 17.186 pts -

Daniel Lara Souza
8° lugar - 17.177 pts -

edps
9° lugar - 16.672 pts -

Andre (pinduvoz)
10° lugar - 15.309 pts